Time and time again, we see how the cybercriminal ecosystem often mirrors what happens in the business world. This can be a criminal group emulating corporate job advertisements in order to recruit accomplices, or a forum operator using modern website design and user experience features to attract customers.
One day while using our strategic partner’s investigation tool, a network of typosquat domains was found. Typosquats involve changing a character in a URL so that it still looks like the original domain at first glance; for example, changing an “m” to an “rn”. We see squats all the time, but what caught our eye was that these weren’t for legitimate businesses, they were for criminal dark web sites, specifically on the Tor network.
Typosquats on criminal markets: No honor among thieves
Anyone browsing Tor will have seen similar images to these (Figure 1), where website owners highlight the legitimate .onion domains for a specific service to protect customers from scammers. We’ve seen these on marketplaces such as Dream Market, Wall Street, and even AlphaBay before it was taken down. The threat of typosquat domains on the dark web are significantly higher for these services because .onion domains are intentionally complex, often appearing as a long set of random characters; they’re called “hidden services” for a reason.
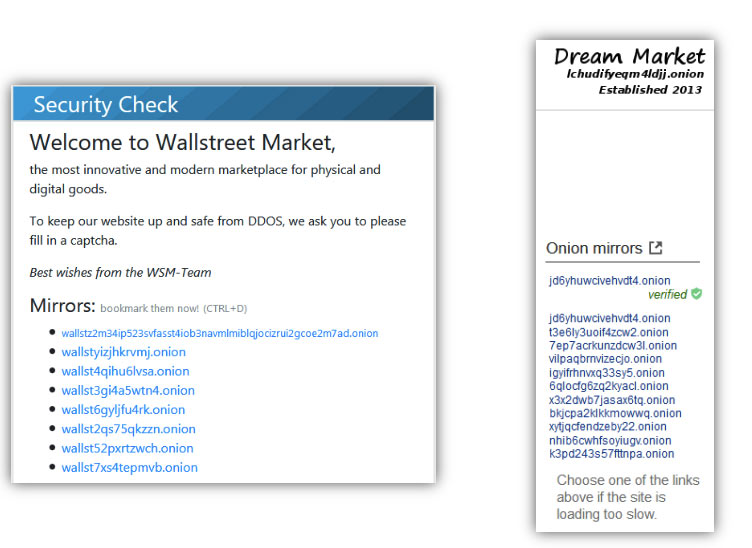
Figure 1: Dark Web marketplaces displaying mirror domains for their sites
Here is an example of what we’re talking about: a legitimate domain for the Tochka/Point Marketplace is “tochka3evlj3sxdv[.]onion” and the typosquat is “tochka3evevasc32[.]onion”.
Again, security people at corporations in every vertical know this issue exists for their businesses and it can lead to a loss in revenue, customer trust and decline in brand reputation. Taking it to the extreme, what if one person or entity created an entire network of exact replica websites of all the companies operating in your vertical? That’s exactly what we found for dark web hidden services like AlphaBay, Hidden Answers, Valhalla, Grams, Hansa Market and others.
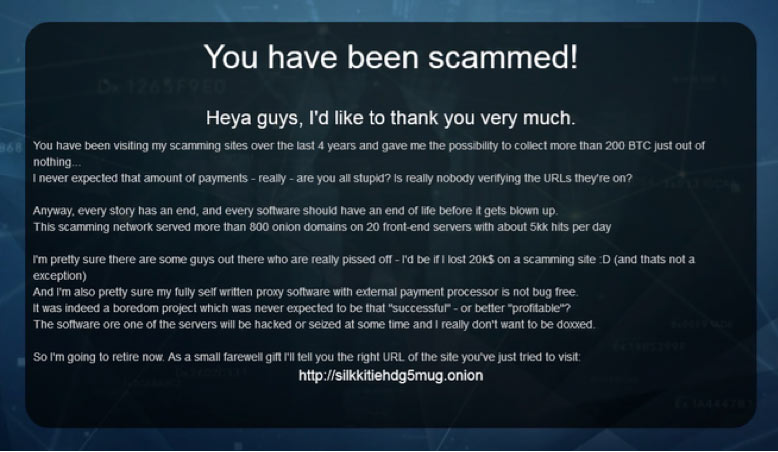
Figure 2: Splash page discovered on several dark web typosquat domains
When our strategic partner first came across this splash page in late November 2018, they really didn’t think much about it. One scam site on Tor is hardly surprising. But when they kept seeing them in relation to several popular marketplaces and forums, it got them interested. A network of typosquats operating for four years, with 800 domains, all owned by the same person or entity? Can that be proven? So, doing some quick research of a unique string in the note on the site’s homepage brought back something similar to the following:
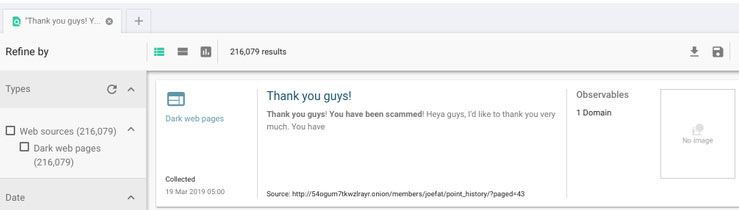
Figure 3: Using our strategic partner’s search application to identify over 200,000 dark web pages containing strings from the scam note
Wow – 216,079??

That seems like a lot, which got us interested even more. Leveraging our strategic partner’s data science colleagues, they were able to aggregate and duplicate all of these results and found over 350 unique .onion domains were being used to spoof “legitimate” dark web domains.
That is a big drop from the original 216,000; this is due to a couple of different reasons. For one, a large proportion of the sites on the dark web act as mirrors to the legitimate version of a dark web service (examples of this are in Figure 1). The other reason is more technical, but mainly involves the way that our strategic partner’s platform collects data. Using our Tochka example from earlier, tochka3evevasc32[.]onion and tochka3evevasc32[.]onion/forum/ and tochka3evevasc32[.]onion/forum/section_1/ were all collected and included within the initial 216,000 number. If you were to visit each of those pages, you would get that same splash page pictured in Figure 2. Extrapolating that to scale across the entire dark web collection, and that 216,000 becomes clearer.
With the dark web being so volatile (sites go up and down all the time) and certain sections being gated or requiring access permissions, it is a tricky thing to have complete visibility over, especially for everyday users. Several directory sites for hidden services exist, which attempt to collect the various domains for these services but could include non-legitimate links (like typosquats). We detected several of these directory sites listing website titles of “Thank you guys!”, indicating these were hosting the Figure 2 splash page. Searching across several of these directories put the number closer to 500. Given this, the 800 domains the fraudster claimed to have in their network could be possible based on these numbers.
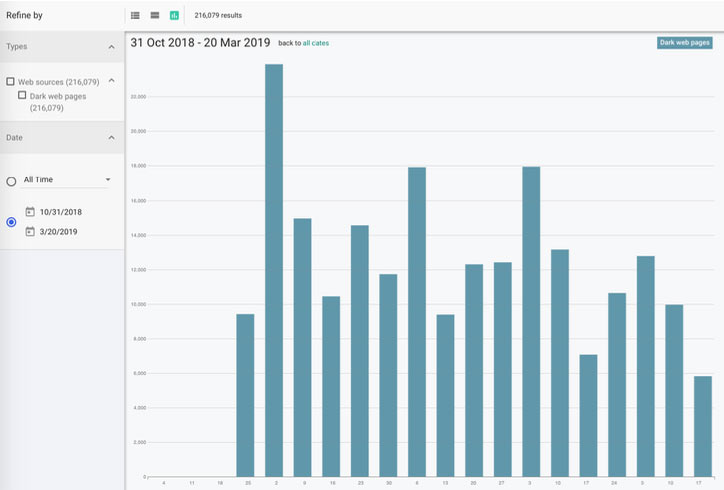
Figure 4: Search results of the unique string between November 2018 and March 2019
Some of these sites were even reported as scams previously, though it’s not clear how widespread this knowledge was among users of these services. We detected posts on lesser known and obscure forums containing scam claims for a few of the domains now hosting the splash page (Figure 4).
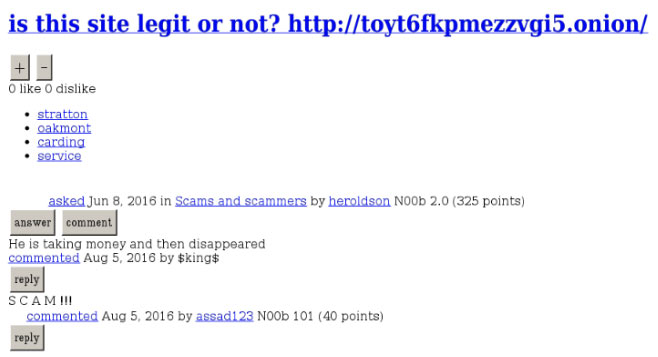
Figure 4: Users questioning the legitimacy of one of the domains controlled by the scammer
How cybercriminals profit from brand impersonation
Scammers are scamming. So, what?
This may not seem like a very big revelation; a scammer creating typosquat domains to conduct fraud against users of the legitimate domain. However, this can provide a good case study of what happens if the issue of typosquatting gets out of hand and taken to the extreme. The scammer claimed that they made off with a lot of money: 200 BTC, which is around $760,000 at the time of writing. That’s nothing to scoff at. If what the fraudster says is true, it proves how profitable brand impersonation and domain squatting can be.
Scammers can monetize their typosquat domains in a variety of ways, including advertising through web traffic driven to the site, harvesting credentials to sell or reuse in other fraud attacks, or directly from purchases made on these sites with no actual product being delivered. Additionally, we’ve observed some of the sites using their own Bitcoin wallets to accept donations for providing the service – a common practice for dark web sites. Though we cannot confirm that the scammer operating this typosquat network was able to get the amount of Bitcoin that they claim, they mention using a self-made payment processor on the sites, indicating that some form of purchasing was occurring.
Of course, there are several regulations and legalities which exist for clear web domains like the Internet Corporation for Assigned Names and Numbers (ICANN) and domain registries, adding more visibility into who owns a site and what they can and cannot do with it (from an impersonation perspective). This also provides more possibilities for reporting and taking down such fraudulent sites. But in 2018 alone, our strategic partner raised over 45,000 typosquat alerts to our clients, which we also help them to remediate through managed takedowns.
Improving your online brand security
Threat actors are going to continue trying to bank off of the prestige and public knowledge of well-known brands to conduct their fraudulent activities, like hosting typosquat domain websites. This is why online brand security is so important for companies operating in the digital age. When it comes to brand security, companies can do the following:
- Monitor for typosquats and potentially purchase domains similar to yours to prevent their use by malicious actors.
- Detect outdated certificates so a malicious actor doesn’t take over legitimate domains.
- Remove spoof social media profiles or mobile applications used to impersonate your brand.
This squatting network proves that brand impersonation that goes unchecked, undetected, and unmitigated can directly lead to loss of consumer trust and incoming revenue.
Guard Street provides threat intelligence for organizations and we will detect the threats covered in this blog. To stay up to date with the latest digital risk and threat intelligence news, subscribe to our threat intelligence emails here. Or, request a threat intelligence demo at www.guardstreetcyberpro.com.


